148 INFORMATION TECHNOLOGY RISK MANAGEMENT1
a. IT infrastructure and operations. Inherent IT risks of a BSFI largely depend on the degree of automation of core processes and applications, the size of branch networks, and the characteristics of its IT organization. BSFIs with larger branch networks and more complex organizational structures usually require a higher degree of reliance on IT systems/infrastructure, which in turn, carry higher levels of inherent IT risks. Interconnectivity risks also play a factor in determining IT risk levels since added connections to third party networks increase complexity as well as exposure to potential information security/cybersecurity risks. These include participation in electronic payment systems and interconnections with other financial institutions, business partners, customers, and third party service providers, among others.
b. Digital/Electronic financial products and services. Digital/electronic financial products and services provided to the BSFI’s corporate and retail clients, by their very nature, can have a direct impact on IT risks, including information security/cybersecurity risks. This is because these products and services are normally provided via the internet or public networks which are inherently risky. Digital/electronic financial products and services include ATM debit, prepaid and credit cards and e-channels such as ATM terminals, point-of-sale (POS) terminals, internet banking and mobile banking facilities, among others. BSFIs that are more aggressive in providing such services are expected to have greater IT risks.
c. IT projects and initiatives. The extent and nature of the BSFI’s IT projects prospectively impact IT risk exposure and complexity. For instance, developing or acquiring a new core banking system is considered a major project, that if not adequately managed and overseen, may heighten inherent IT risks. Also, IT projects and initiatives entail the use of current resources in terms of funding and manpower that might affect existing IT operations and risk profile.
d. Outsourced services. While outsourcing in general does not diminish the BSFI’s responsibility over the function/service outsourced, outsourcing poses an added dimension to IT and information security risks. For this reason, outsourcing arrangements require a higher degree of oversight, due diligence, and risk management controls. Outsourcing core IT services and functions via cloud computing platforms may further intensify IT and information security risks.
e. Systemic importance. The systemic importance of a BSFI is a critical determinant in assessing inherent IT and information security/cybersecurity risks since BSFIs identified as “Domestic Systemically Important Banks” or DSIBs are essentially larger in size and have more complex operations and product offerings. Moreover, cyber-attacks against DSIBs can have serious implications to financial and economic stability that may undermine public trust and confidence in the financial system.
f. Threats. The volume, type, and severity of cyber-attacks and fraud targeting a specific BSFI affects IT and cybersecurity risk profiles. Some BSFIs may be more prone to attacks compared to others by virtue of their asset size, customer base, systemic importance, and other factors. Thus, BSFIs that are likely targets of these types of threats should have greater degree of cyber-preparedness and resilience.
| IT Profile Classification | General Description/Attributes |
| Complex | A BSFI with complex IT profile uses technology extensively in supporting mission-critical business processes and delivering financial products and services. It has ubiquitous branch network in the country and offers a wide array of digital/electronic financial products and services to a large number of corporate and retail clients. It is highly interconnected with external third party stakeholders and actively participates in electronic payment systems and networks, usually involving large-value transfers. Business strategies and objectives are largely anchored on IT platforms, digital innovation, and technology-based solutions. It is also aggressively utilizing/exploring emerging technologies such as cloud computing, social media and big data. |
| Moderate | A BSFI classified as moderate uses technology to some extent, but not as aggressively as those classified as complex. Its branch network, IT organization and structure, and extent of IT projects are also relatively less significant than those of complex BSFIs. IT applications and systems are integrated but primarily support traditional banking products and services. It may offer basic digital/electronic products and services, such as ATM terminals/card-based products, to a limited number of clients. |
| Simple | A BSFI classified as simple generally has very limited use of technology with minimal interconnectivity to its clients and other institutions. Likewise, branch network or geographic presence is confined to a specific locality. IT applications and systems are stand-alone or are not fully integrated and e-banking products and services are rarely offered. A simple BSFI also has few IT personnel and customer base. |
| 4 | BSFIs with this rating exhibit strong performance in every respect. Noted weaknesses in IT are minor in nature and can be easily corrected during the normal course of business. |
| 3 | BSFIs with this rating exhibit satisfactory performance but may demonstrate modest weaknesses in operating performance monitoring, management processes or system development. |
| 2 | BSFIs with this rating exhibit less than satisfactory performance and require considerable degree of supervision due to a combination of weaknesses that may range from moderate to severe. |
| 1 | BSFIs with this rating exhibit deficient IT environment that may impair the future viability of the entity, thereby requiring immediate remedial action. |
a. Advanced persistent threat or APT shall refer to a sophisticated form of attack that involves coordinating multiple methods of identifying and exploiting a target’s vulnerabilities over an extended period to do harm.
b. Card skimming shall refer to the illegal copying of information from the magnetic stripe of a credit or ATM card to gain access to accounts.
c. Cloud computing shall refer to a model for enabling ubiquitous, convenient, and on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction.
d. Compromised state shall refer to a state wherein someone or something has maliciously broken into networks, systems and computers which raises doubt as to the integrity of information assets, such as but not limited to, program files, image files, and operating system files.
e. Cyber-threat shall refer to a deliberate act of omission or commission by any person carried out using the internet and/or other electronic channels, in order to communicate false or fraudulent representations to prospective victims, to conduct fraudulent transactions, or to illegally obtain proprietary data or information related to the institution, their customers and other stakeholders. Cyber-threat can be used synonymously with cyber-fraud, cyber-attack or cyber-related incidents.
f. Cybersecurity shall refer to technologies, processes, and practices designed to protect a BSFI’s information assets and consumers by preventing, detecting, and responding to cyber-attacks.
g. Data breach shall refer to an incident in which sensitive, protected or confidential data or information has potentially been viewed, stolen, leaked used, or destroyed by unauthorized persons.
h. Defense-in-depth shall refer to a security strategy or design of deploying security controls over multiple or various layers across the network, systems, and applications such that a failure in one control would be compensated by another control in the next layer. This approach effectively delays or disrupts an attacker’s ability to progress within the attack sequence.
i. Distributed denial of service (DDoS) shall refer to a type of attack which makes use of the capacity limitation of enterprise networks, systems or ingress with extreme traffic loads.
j. Hacking shall refer to unauthorized access into or interference in networks, systems and computers without the knowledge and consent of the system/information owner.
k. Information security program (ISP) shall refer to information security policies, standards and procedures, security operations, technologies, organizational structures, and information security awareness and training programs aimed at protecting a BSFI’s information assets and supporting infrastructure from internal and external threats.
l. Information security strategic plan (ISSP) shall refer to the roadmap to guide a BSFI in transforming the current state of security to the desired state taking into account business goals and strategies.
m. Information security risk management (ISRM) shall refer to the process of identifying, assessing, mitigating, managing, and monitoring information security risks, including cyber-risk, to ensure these are within acceptable levels. It should be integrated into the BSFI’s ISP and enterprise-wide risk management system.
n. Malware shall refer to malicious software that compromises the confidentiality, availability or integrity of information systems, networks or data. Examples of malware include ransomware, trojans, adware, botnets, bugs, and spyware, among others.
o. Pharming shall refer to a form of cyber-attack that redirects a website traffic to another fake website to obtain user credentials and information.
p. Phishing shall refer to the use of electronic communications such as e-mail to masquerade with trusted identity to capture sensitive information to gain access to accounts. It involves tricking customers into giving sensitive information through fraudulent emails or websites.
q. Reportable major cyber-related incidents shall refer to any cyber-related incidents that meet the criteria for reporting/notification to the Bangko Sentral as laid out in Item “a(2)(a)” of this Section (Reporting and notification standards).
r. Security operations center (SOC) shall refer to a unit or function that provides centralized visibility, continuous monitoring, and rapid response and recovery procedures on security incidents and events.
s. Spearphishing shall refer to a more advanced type of phishing attack which is customized to a particular target (e.g., executives, privileged users, etc.).
t. Threat actor shall refer to a person, group or nation/state/government that carries out or intends to carry out damaging acts against another party. An advanced threat actor shall refer to a person, organized group, or nation/state/government that (a) possesses superior capabilities, resources and skills to launch sophisticated cyber-attacks; or (b) seeks military and/or intelligence information for cyber-espionage purposes.
u. Threat intelligence shall refer to the process of gathering and analyzing information about the proficiencies, tactics, and motives of malicious actors/attackers that enables a BSFI to institute appropriate countermeasures quickly.
a. Operational risk is the risk to earnings and capital arising from problems with service or product delivery. This risk is a function of internal controls, IT systems, employee integrity and operating processes. Operational risk exists in all products and services;
b. Strategic risk is the risk to earnings and capital arising from adverse business decisions on IT-related investments or improper implementation of those decisions. The risk is a function of the compatibility of an organization’s strategic goals, the business strategies developed to achieve those goals, the resources deployed against these goals and the quality of implementation. The resources needed to carry out business strategies are both tangible and intangible which include communication channels, operating systems, delivery networks and managerial capacities and capabilities;
c. Reputational risk is the risk to earnings and capital arising from negative public opinion. This affects the institution’s ability to establish new relationships or services or continue servicing existing relationships. The risk can expose the institution to litigation, financial loss or damage to its reputation; and
d. Compliance risk is the risk to earnings and capital arising from the violations of, or non-conformance with laws, rules and regulations, prescribed practices or ethical standards. Compliance risk also arises in situations where the laws and rules governing certain products activities of the BSFI’s clients may be ambiguous or untested. Compliance risk exposes the institution to monetary penalties, non-monetary sanctions and possibility of contracts being annulled or declared unenforceable.
a. IT Governance. This is an integral part of BSFIs’ governance framework and consists of the leadership and organizational structures and processes that ensure the alignment of IT strategic plan with BSFIs’ business strategy, optimization of resources management, IT value delivery, performance measurement and the effective and efficient use of IT to achieve business objectives and effective IT risk management implementation. BSFIs must establish an effective IT governance framework covering the following:
(1) Oversight and organization of IT functions. Accountability is a key concern of IT governance and this can be obtained with an organizational structure that has well-defined roles for the responsibility of information, business processes, applications, IT infrastructure, etc.
(2) IT policies, procedures and standards. IT controls, policies, and procedures are the foundation of IT governance structure. It helps articulate the rules and procedures for making IT decisions, and helps to set, attain, and monitor IT objectives.
• IT Governance/ Management;
• Development and Acquisition;
• IT Operations;
• Communication networks;
• Information security;
• Electronic Banking/Electronic Products and Services; and
• IT Outsourcing/Vendor Management.
(3) IT audit. Audit plays a key role in assisting the board in the discharge of its corporate governance responsibilities by performing an independent assessment of technology risk management process and IT controls.
• Independence of the IT audit function and its reporting relationship to the Board or its Audit Committee;
• Expertise and size of the audit staff relative to the IT environment;
• Identification of the IT audit universe, risk assessment, scope, and frequency of IT audits;
• Processes in place to ensure timely tracking and resolution of reported weaknesses; and
• Documentation of IT audits, including work papers, audit reports, and follow-up.
(4) Staff competence and training. The rapid development in technology demands appropriate, skilled personnel to remain competent and meet the required level of expertise on an ongoing basis.
(5) Management Information Systems (MIS). The BSFIs’ IT organization often provides an important support role for their MIS. Accurate and timely MIS reports are an essential component of prudent and reasonable business decisions. At the most senior levels, MIS provides the data and information to help the Board and management make strategic decisions. At other levels, MIS allows management to monitor the institution’s activities and distribute information to other employees, customers, and members of management.
(6) IT risk management function. Management of risk is a cornerstone of IT Governance. BSFIs should have a policy requiring the conduct of identification, measurement, monitoring and controlling of IT risks for each business function/service on a periodic basis. BSFIs should define and assign these critical roles to a risk management unit or to a group of persons from different units collectively performing the tasks defined for this function.
• a description of risk being considered for acknowledgement by owner of risk and an assessment of the risk that is being accepted;
• identification of mitigating controls;
• formulation of a remedial plan to reduce risk; and
• approval of risk acknowledgement from the owner of the risk and senior management.
b. Risk identification and assessment. BSFIs should maintain a risk assessment process that drives response selection and controls implementation. An effective IT assessment process begins with the identification of the current and prospective IT risk exposures arising from the institution’s IT environment and related processes. The assessments should identify all information assets, any foreseeable internal and external threats to these assets, the likelihood of the threats, and the adequacy of existing controls to mitigate the identified risks. Management should continually compare its risk exposure to the value of its business activities to determine acceptable risk levels.
c. IT controls implementation. Controls comprise of policies, procedures, practices and organizational structures designed to provide reasonable assurance that business objectives will be achieved and undesired events will be mitigated. Management should establish an adequate and effective system of internal controls based on the degree of exposure and the potential risk of loss arising from the use of IT. Controls for IT environment generally should address the overall integrity of the environment and should include clear and measurable performance goals, the allocation of specific responsibilities for key project implementation, and independent mechanisms that will both measure risks and minimize excessive risk-taking. BSFI Management should implement satisfactory control practices that address the following as part of its overall IT risk mitigation strategy: 1) Information security; 2) Project management/development and acquisition and change management; 3) IT operations; 4) IT outsourcing/Vendor management; and 5) Electronic banking, Electronic payments, Electronic money and other Electronic products and services.
(1) Information security. Information is a vital asset of a BSFI that must be adequately protected and managed to preserve its confidentiality, integrity and availability. Considering the crucial role information plays in supporting business goals and objectives, driving core operations and critical decision-making, information security is intrinsically linked to the overall safety and soundness of BSFIs. Thus, the BSFI needs to put in place a robust, resilient and enterprisewide framework for ISRM supported by effective information security governance and oversight mechanisms. Information security risk exposures must be managed to within acceptable levels through a dynamic interplay of people, policies and processes, and technologies and must be integrated with the enterprise-wide risk management system.
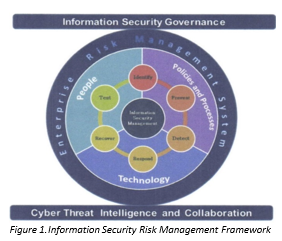
The ISRM framework is based upon the following underlying fundamental principles and concepts:
(a) Strong leadership and effective Information Security (IS) governance and oversight. The BSFI’s board and senior management set the overall tone and strategic direction for information security by providing strong leadership, effective information security governance and oversight. They should take the lead in establishing an information security culture that regards security as an intrinsic part of the BSFI’s core business and operations. Instilling a strong security culture ensures that security controls, processes, and measures are deeply embedded into the institution’s lines of business, products, services and processes, including its employees and external relationships. The board and senior management should adopt the right mindset and understand the crucial role of information security in supporting/achieving business goals and objectives. Towards this end, they should oversee the development of an information security strategic plan (ISSP) to clearly articulate security strategies and objectives aligned with business plans.
(b) Integrated, holistic and risk-based approach. The ISRM should form an integral part of the BSFI’s ISP and enterprise risk management system. It encompasses the people, policies and processes, and technology elements in the organization that should be harmonized to support information security goals and objectives. Information security is not achieved by merely focusing on technology or one aspect and no one element is superior over the other. Each of these elements must work together to achieve the desired security posture and manage information security risks to acceptable levels. In line with the increasing interconnectivity of BSFIs and other industry players, the ISRM should also consider security controls and requirements over third party service providers, customers, banks, and other third party stakeholders which are linked or have access to the BSFI’s network and systems. This is because threat actors may launch their attacks on the BSFI through these third party networks.
(c) Continuing cycle. The ISRM involves a continuing cycle consisting of the following six (6) major phases:
(i) Identify. The starting point of the cycle is the identification of the BSFI’s information security as well as cyber-related risks. Under this phase, management needs to identify its business processes and functions, information assets classified as to sensitivity and criticality, threats and vulnerabilities, interconnections, and security architecture. Identification of these factors facilitates BSFI’s understanding and assessment of its inherent information security and cyber risks which are key inputs in determining, designing, and implementing the appropriate risk treatment options.
(ii) Prevent. After identifying these key factors and assessing the information security and cyber risks, the prevent phase comes into play where adequate protection mechanisms and controls are designed and implemented. These include measures ranging from baseline to advanced tools and approaches such as defense-in-depth, malware prevention, access controls and cybersecurity awareness programs, among others. These preventive controls are generally categorized into three (3) types, as follows:
(aa) Administrative controls – refer to the policies, standards, and procedures in place which articulate Management’s intent, expectations, and direction on information security. It also includes security trainings and awareness programs and personnel security practices designed to prevent unwarranted employee behavior.
(bb) Physical and environmental controls – pertain to the security controls and measures implemented to protect physical infrastructure such as data centers, computer facilities, and equipment from damage, unauthorized access or environmental hazards.
(cc) Technical controls – refer to the logical security controls, security tools, and technologies to ensure that the confidentiality, integrity, and availability objectives for information assets are achieved.
(iii) Detect. Detection capabilities should also be in place as prevention alone is not sufficient. As demonstrated in recent cyberattacks, the ability of an institution to quickly detect anomalous activities and evaluate the scope of an attack is an important aspect in significantly reducing negative impacts. Management should design and implement effective detection controls over the BSFI’s networks, critical systems and applications, access points, and confidential information.
(iv) Respond. The response phase is triggered upon confirmation of an occurrence of a cyber-attack or security incident affecting the BSFI and its customers. With the growing incidence of sophisticated cybercrimes and threats, the BSFI should be prepared to respond quickly considering that cyber-attacks are no longer a remote possibility. Therefore, it should develop comprehensive, updated, and tested incident response plans supported by well-trained incident responders, investigators, and forensic data collectors. Through adequate response capabilities, the BSFI should be able to minimize and contain the damage and impact arising from security incidents, immediately restore critical systems and services, and facilitate investigation to determine root causes.
(v) Recover. This phase encompasses both the resumption of activities at a level which is considered “good enough for a certain period of time” and full recovery, i.e., an eventual return to full service. Management should be able to establish back-up facilities and recovery strategies to ensure the continuity of critical operations. During the recovery phase, it should ensure that information processed using back-up facilities and alternate sites still meet acceptable levels of security. To achieve cyber resilience, the BSFI should consider information security incidents and cyber-related attack scenarios in its business continuity management and recovery processes.
(vi) Test. The BSFI needs to continually assess and test controls and security measures implemented under the prevent, detect, respond, and recover phases to ensure that these are effective and working as intended. Likewise, a comprehensive, systematic and layered testing and assurance program covering security processes and technologies should be in place. This is to ensure that the ISRM is on track in providing appropriate level of information security commensurate with the BSFIs’ IT profile complexity. This phase also ensures that both the ISSP and ISP remain effective vis-a-vis the fast-evolving cyberthreat landscape.
(d) Cyber threat intelligence and collaboration. In response to the growing cyber-threat landscape, BSFIs need to step up their information security posture and resilience beyond their respective networks. Likewise, BSFIs need to enhance situational awareness that would provide a keen sense of the threat landscape as it relates to their IT risk and cyber-risk profiles, operating complexities, and business models. Further, BSFIs need to collaborate with each other, including regulators, law enforcement agencies, and other third party stakeholders for a collective, coordinated, and strategic response through information sharing and collaboration. Information sharing allows BSFIs to enhance threat intelligence that enables quick identification, prevention and response to emerging and persistent threats. (Detailed guidelines/standards on information security are shown in Appendix 75)
(2) Project management/development and acquisition and change management. BSFIs should establish a framework for management of IT-related projects. The framework should clearly specify the appropriate project management methodology that will govern the process of developing, implementing and maintaining major IT systems. The methodology, on the other hand, should cover allocation of responsibilities, activity breakdown, budgeting of time and resources, milestones, checkpoints, key dependencies, quality assurance, risk assessment and approvals, among others. In the acquisition and/or development of IT solutions, BSFIs should ensure that business and regulatory requirements are satisfied. (Detailed guidelines/standards on Project Management/Development and Acquisition and Change Management are shown in Appendix 76)
(3) IT operations. IT has become an integral part of the day-to-day business operation, automating and providing support to nearly all of the business processes and functions within the institution. Therefore, the IT systems should be reliable, secure and available when needed which translates to high levels of service and dependency on IT to operate.
(4) IT outsourcing/vendor management program. IT outsourcing refers to any contractual agreement between a BSFI and a service provider or vendor for the latter to create, maintain, or reengineer the institution’s IT architecture, systems and related processes on a continuing basis. A BSFI may outsource IT systems and processes except those functions expressly prohibited by existing regulations. The decision to outsource should fit into the institution’s overall strategic plan and corporate objectives and said arrangement should comply with the provisions of existing Bangko Sentral rules and regulations on outsourcing. Although the technology needed to support business objectives is often a critical factor in deciding to outsource, managing such relationships should be viewed as an enterprise-wide corporate management issue, rather than a mere IT issue.
(5) Electronic products and services. The evolution in technology revolutionized the way banking and financial products and services are delivered. Physical barriers were brought down enabling clients to access their accounts, make transactions or gather information on financial products and services anywhere they are, at any time of the day and at their own convenience. As development in technology continues to accelerate, innovative electronic products and services are foreseen to bring more accessibility and efficiency. However, BSFIs may be confronted with challenges relating to capacity, availability and reliability of the electronic services. Likewise, fraudulent activities via electronic channels are also rising in number.
(a) The entire ATM system shall be upgraded/converted to allow adoption of end-to-end Triple DES (3DES) encryption standards by 01 January 2015. The 3DES encryption standards shall cover the whole ATM network which consists of the host processors, switches, host security module (HSM), automated teller machines (ATMs), point-of-sale (POS) terminals and all communication links connected to the network;
(b) ATMs to be installed after 04 September 2014 should be 3DES compliant; and
(c) ATMs, POS terminals and payment cards are also vulnerable to skimming attacks due to the lack of deployment of globally recognized EMV enabled technology by BSFIs. Magnetic stripe only ATMs, POS Terminals and cards are largely defenseless against modern fraud techniques. Therefore, all concerned BSFIs should shift from magnetic stripe technology to EMV chip-enabled cards, POS Terminals and ATMs. The entire payment card network should be migrated to EMV. This requirement shall cover both issuing and acquiring programs of concerned BSFIs. A written and board-approved EMV migration plan should be submitted to the appropriate supervising department of the Bangko Sentral within six (6) months from 22 August 2013. The guidelines on EMV Implementation are shown in Appendix 112. The guidelines on the EMV Card Fraud Liability Shift Framework (ECFLSF) are in Appendix 113 3.
d. Risk measurement and monitoring. BSFI Management should monitor IT risks and the effectiveness of established controls through periodic measurement of IT activities based on internally established standards and industry benchmarks to assess the effectiveness and efficiency of existing operations. Timely, accurate, and complete risk monitoring and assessment reports should be submitted to management to provide assurance that established controls are functioning effectively, resources are operating properly and used efficiently and IT operations are performing within established parameters. Any deviation noted in the process should be evaluated and management should initiate remedial action to address underlying causes. The scope and frequency of these performance measurement activities will depend on the complexity of the BSFI’s IT risk profile and should cover, among others, the following:
(1) Performance vis-à-vis approved IT strategic plan. As part of both planning and monitoring mechanisms, BSFI management should periodically assess its uses of IT as part of overall business planning. Such an enterprise-wide and ongoing approach helps to ensure that all major IT projects are consistent with the BSFI’s overall strategic goals. Periodic monitoring of IT performance against established plans shall confirm whether IT strategic plans remain in alignment with the business strategy and the IT performance supports the planned strategy.
(2) Performance benchmarks/service levels. BSFIs should establish performance benchmarks or standards for IT functions and monitor them on a regular basis. Such monitoring can identify potential problem areas and provide assurance that IT functions are meeting the objectives. Areas to consider include system and network availability, data center availability, system reruns, out of balance conditions, response time, error rates, data entry volumes, special requests, and problem reports.
(3) Quality assurance/quality control. BSFI should establish quality assurance (QA) and quality control (QC) procedures for all significant activities, both internal and external, to ensure that IT is delivering value to business in a cost effective manner and promotes continuous improvement through ongoing monitoring. QA activities ensure that product conforms to specification and is fit for use while QC procedures identify weaknesses in work products and to avoid the resource drain and expense of redoing a task. The personnel performing QA and QC reviews should be independent of the product/process being reviewed and use quantifiable indicators to ensure objective assessment of the effectiveness of IT activities in delivering IT capabilities and services.
(4) Policy compliance. BSFIs should develop, implement, and monitor processes to measure IT compliance with their established policies and standards as well as regulatory requirements. In addition to the traditional reliance on internal and third party audit functions, BSFIs should perform self-assessments on a periodic basis to gauge performance which often lead to early identification of emerging or changing risks requiring policy changes and updates.
(5) External assessment program. Complex BSFIs may also seek regular assurance that IT assets are appropriately secured and that their IT security risk management framework is effective. This may be executed through a formal external assessment program that facilitates a systematic assessment of the IT security risk and control environment over time.
a. Reporting requirement. BSFIs are required to submit to the Bangko Sentral the following reports/information:
(1) Periodic reports. BSFIs shall submit an Annual IT Profile, as listed in Appendix 7, electronically to the appropriate supervising department of the Bangko Sentral within twenty five (25) days from the end of reference year.
(2) Event-driven reports. BSFIs shall notify the Bangko Sentral upon discovery of any of the following:
(i) resulted in an unauthorized access and infiltrati on into the BSFI’s internal network (i.e., hacking, advanced persistent threats, presence of malware);
(ii) involved a system-level compromise (i.e., attacks on BSFI’s core systems, as opposed to phishing attempts of individual clients);
(iii) affected a significant number of customer accounts simultaneously;
(iv) involved significant data loss or massive data breach;
(v) indicated spearphishing attacks targeting the BSFIs’ directors, senior executives, officers, or privileged users;
(vi) resulted in the unavailability of critical systems/services (e.g., Distributed Denial of Service (DDoS) attack resulting in service outage);
(vii)inflicted material financial losses to the BSFIs, their customers and other stakeholders; or
(viii) has been suspected to be perpetrated by an advanced threat actor.
(b) Disruptions of financial services and operations. These include disruption of critical operations which lasts for more than two (2) hours due to internal and external threats, which may be natural, man-made or technical in origin. Such scenarios usually involve loss of personnel, technology, alternate site, and service providers. Causes of such interruptions include, but are not limited to fire, earthquakes, flood, typhoon, long-term power outage, technical malfunctions, pandemics and other threats.
b. Procedure for event-driven reporting. The following procedures shall be followed by BSFIs in reporting reportable major cyber-related incidents and/or disruptions of financial services and operations stated in Item “(a)2” of this Section (Reporting and Notification Standards):
(1) The BSFIs’ Compliance Officer and/or BSFI-designated Officer shall notify the appropriate supervising department of the Bangko Sentral within two (2) hours from discovery of the reportable major cyber-related incidents and/or disruptions of financial services and operations stated in Item “a(2)” of this Section (Reporting and Notification Standards), in accordance with Appendix 7.
(2) The BSFIs shall disclose, at the minimum, the nature of the incident and the specific system or business function involved.
(3) Within twenty-four (24) hours from the time of the discovery of the reportable major cyber-related incident and/or disruption, a follow-up report should be sent to the appropriate supervising department of the Bangko Sentral through e-mail indicating the following, as applicable:
(a) nature of the incident;
(b) manner and time of initial detection;
(c) impact of the incident based on initial assessment (e.g., length of downtime, number of affected customers/accounts, number of complaints received, value of transactions involved);
(d) initial response or actions taken/to be taken (e.g., conduct of root cause analysis) with respect to the incident; and
(e) information if the incident resulted in activation of the Business Continuity Plan (BCP) and/or Crisis Management Plan (CMP).
c. Verification of root cause. Depending on the nature and severity of the reported incident/disruption, the Bangko Sentraal may require BSFIs to provide additional information or updates until the matter is satisfactorily resolved. Likewise, the Bangko Sentral may conduct special examination or overseeing inspection, if necessary, to verify root cause of the incident, assess the impact to the BSFI and the financial system as a whole, identify areas for improvement to prevent recurrence of the incident, and promote enterprise and industry-wide operational resilience.
d. Compliance with reporting of crimes and losses. Compliance with event-driven report requirement shall not excuse BSFIs from complying with the existing rules on the reporting of crimes and losses under Sec. 173 (Report on crimes/losses). Likewise, any cyber-related incident which does not qualify as a reportable major cyber-related incident and other disruptions arising from crimes and losses must be reported to the Bangko Sentral in accordance with the aforesaid regulations. Operational risk events which are covered under Item “a(2)” on the event-driven reporting and notification requirements shall no longer require separate reporting and notification pursuant to Sec. 146 (Notification/Reporting to Bangko Sentral).
e. Information gathering. Should the conduct of in-depth studies and research on certain technology development or key area of concern relating to technology risk and cybersecurity be warranted, the Bangko Sentral, from time to time, may request BSFIs to submit specific data and information thereon through surveys, questionnaires or other means.
a. Non-compliance with the requirements in Item “b” of this Section (Reporting and notification standards) will be subject to “High” penalty level monetary sanctions pursuant to Sec. 1102 (Guidelines on the imposition of monetary penalties).
b. Consistent with Sec. 002, the Bangko Sentral may deploy applicable enforcement actions on the BSFI and/or its directors, officers, and/or employees for violations on this requirement.
c. Annual IT Profile and other periodic reports which have been considered as erroneous, delayed or unsubmitted shall be subject to the penalties for Category B reports under Section Sec. 171 (Sanctions on reports for non-compliance with the reporting standards).
(Circular Nos. 1019 dated 31 October 2018, 982 dated 9 November 2017, 958 dated 25 April 2017, 936 dated 28 December 2016, 859 dated 24 November 2014, and 833 dated 28 May 2014)
Footnotes
- BSFIs shall comply with the Enhanced Guidelines on Information Security Management within a period of one (1) year from 5 December 2017. In this regard, a BSFI should be able to show its plan of actions with specific timelines, as well as the status of initiatives being undertaken to fully comply with the provisions of this circular, upon request of the Bangko Sentral starting December 2017.
- US National Institute of Standards and Technology (NIST), ISO/IEC, ISACA and Committee and Payments and Market Infrastructures (CPMI), among others.
- This paragraph shall take effect on 01 January 2017.
